Cisco Asdm 7.2 For Asa 5510 Download
If you have ASA 5510 Old one not any X Model. As for as i know you can max of 9.1.7 interim. With ASDM 7.8.X. Couple of steps to keep in mind before upgrade: 1. Read the release notes which you upgrading. If your old code older than 8.2 then you need to look NAT conversion. Take backup config all the time. I used the ASA 5510 for most of these examples. The big difference between the ASA 5505 and all the other models is that it’s the only firewall that has 4 switchports. The 5510 only has L3 interfaces, it doesn’t have switchports.
- This is a small howto on backup your CISCO ASA 5510 config via ASDM & TFTP running on your windows pc. First download WINAGENTS TFTP Server application (Its a small utility) and can be installed on any version of windows you are running. Installation is traditionally simple by clicking on Next button. 1- Install WINAGENTS TFTP SERVER 2- Start.
- ASDM7.6.1 and 7.6.2 are available as download for the ASA 5510 on the Cisco download page, and according to the comment, it is compatible with all firmware versions from 8.0 to 9.6 (but there isn't a firmware version newer than 9.1.7 (16) for ASA 5510). Where did you read, that ASDM7.6 is not compatible with firmware 9.1 on ASA 5510?
Apr 30, 2009 · The Cisco ASA supports a variety of features that can be customized for the clientless SSL VPN user experience, among which are portal look and feel, application access, and file browsing. Configure the Crypto Map¶ Only a single Crypto Map can be bound to an interface, so if one already exists use a different sequence number to existing entries. If remote access is configured it is important to ensure that site-to-site entries have a lower sequence nubmer than the remote access one.
The ASA software has a similar interface to the Cisco IOS software on routers. There is a command line interface (CLI) that can be used to query operate or configure the device. In config mode the configuration statements are entered. The configuration is initially in memory as a running-config but would normally be saved to flash memory. Cisco Firewall :: ASA 5510 Identity NAT Configuration For Remote Access VPN And Site-to-Site Mar 9, 2011. I am try to configure ASA 5510 with 8.3 IOS version.My internal users are 192.168.2.0/24 and i configured dynamic PAT and are all internet . Jun 30, 2017 · Cisco prepared multiple Cisco ASA firewalls to fit your network of all sizes. ASA 5505 and ASA 5500-X Series (such as the ASA 5505, ASA 5510,ASA 5512-X, and ASA 5515-X) were designed for small and branch offices. To meet specific… its massive config and we have many many tunnel terminated on ASA i don't know what specific you looking for. I don't know what portion i should put here and omit all security stuff, it would be massive cut paste for me. if you point specific section i can do that, all i want to know how IPsec VPN know or route remote subnet traffic, there is no route command i can use to tell route 172.20.0.0 . Petes-ASA(config-webvpn)# tunnel-group-list enable Petes-ASA(config-webvpn)# anyconnect image disk0:/anyconnect-win-4.8.02042-webdeploy-k9.pkg 1 Petes-ASA(config-webvpn)# anyconnect enable 4. I’m going to create a LOCAL username and password, I suggest you do the same, then once you have proved it’s working OK, you can. change the . Jul 23, 2014 · Learn how to configure IPSEC VPNs (site-to-site, hub-and-spoke, remote access), SSL VPN, DMVPN, GRE, VTI etc. This book is packed with step-by-step configuration tutorials and real world scenarios to implement VPNs on Cisco ASA Firewalls (v8.4 and above and v9.x) and on Cisco Routers.
Oct 18, 2012 · The Cisco ASA will be acting as the VPN server and the Cisco router will be the client. EzVPN NEM – Network Extension Mode With NEM, you will be able to reach IPs on the client side of the tunnel from the server where was in CLIENT mode, all traffic is PAT from the client router, thus you will only be able to initiate traffic from the client . Jul 23, 2020 · In this course, Enabling Remote Access with Cisco VPNs, you will learn how to configure three different remote access VPNs on Cisco Routers and ASAs. First, you will go through how to generate identity certificates. Next, you will move on to configuring an SSL VPN on an ASA followed by a router. Login to your Cisco firewall ASA5500 ASDM and go to Wizard > IPsec VPN Wizard. and follow up the screens. 2.1 In 'VPN Tunnel Type', choose 'Remote Access' From the drop-down list, choose 'Outside' as the enabled interface for the incoming VPN tunnels. Keep the box checked,'Enable inbound IPSec sessions to bypass interface access lists. Here I'll attempt to give an overview of Cisco ASA's implementation of the static virtual tunnel interface (aka 'SVTI', or 'VTI' for short), also known more simply as 'route-based VPN', and how to configure it on Cisco ASA firewalls.
I have configured a Cisco ASA 5510 via the ASDM for a remote access VPN tunnel. It is configured to do pre-share authentication and then pass user authentication to an IAS server to query against AD. It seems like all is well I am able to authenticate however in the final step which is Negotiating Security Policies it does not ever finish and . Summary. The configuration of a VPN can be daunting, and getting it to work as expected can be very challenging. Cisco's Easy VPN feature allows at least the client configuration to be as easy as possible and enables the relatively small ASA 5505 to become a well-secured, easily configured hardware client. In this lesson we’ll take a look how to configure remote access IPsec VPN using the Cisco VPN client. This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel. The sample configuration connects a Cisco ASA device to an Azure route-based VPN gateway. The connection uses a custom IPsec/IKE policy with the UsePolicyBasedTrafficSelectors option, as described in this article. The sample requires that ASA devices use the IKEv2 policy with access-list-based configurations, not VTI-based. Consult your VPN . Clientless SSL VPN remote access set-up guide for the Cisco ASA by Lori Hyde in Data Center , in Networking on April 22, 2009, 11:30 PM PST The ASA software has a similar interface to the Cisco IOS software on routers. There is a command line interface (CLI) that can be used to query operate or configure the device. In config mode the configuration statements are entered. The configuration is initially in memory as a running-config but would normally be saved to flash memory. This section demonstrates how to configure the Cisco ASA to terminate Cisco VPN client IPSec connections using certificates. The configuration steps to configure remote-access VPNs using preshared keys are covered in Chapter 16, 'Remote Access VPNs.' Figure 17-7 illustrates the topology and components used in the following example. Figure 17-7. This post describes how to build a remote access VPN connection using Clientless SSL VPN feature. Related posts in this blog: Cisco ASA 5500-X Series Software 9.x Configuration Notes (Tips and Tricks) Cisco ASA Remote Access VPN Configuration 2 - Anyconnect VPN Configuration; Cisco ASA Remote Access VPN Configuration 1 - Clientless SSL VPN .
Also, you must purchase and enable an RA VPN license, any of the following: AnyConnect Plus, AnyConnect Apex, or AnyConnect VPN Only. These licenses are treated the same for FTD devices, although they are designed to allow different feature sets when used with ASA Software-based headends. May 26, 2019 · In this article I will walk through the steps that are required to configure the ASA for external authentication using Cisco ISE for remote access VPN users. This demonstration will use the following devices: Cisco ISE 2.4Cisco ASA 9.8Cisco AnyConnect 4.6Test LaptopServer 2012 R2 Overview Cisco ISE can be used to authenticate remote access users… This post describes how to build a remote access VPN connection using Clientless SSL VPN feature. Related posts in this blog: Cisco ASA 5500-X Series Software 9.x Configuration Notes (Tips and Tricks) Cisco ASA Remote Access VPN Configuration 2 - Anyconnect VPN Configuration; Cisco ASA Remote Access VPN Configuration 1 - Clientless SSL VPN . Hello, I have a Cisco 5510 that I had to creat sub interfaces on the inside part of the network due to multiple VLAN's. I am having issues configuring outside VPN access to the VLAN. Mar 11, 2018 · This post only describes configuring a static IP address on a Cisco AnyConnect Remote Access VPN. Refer to the following posts for more detail instructions on how to configure:ASA AnyConnect SSL-VPNASA AnyConnect IKEv2/IPSec VPN […]
Soundarya lahari with meaning in telugu pdfSearch for jobs related to Remote access vpn cisco asa 5510 or hire on the world's largest freelancing marketplace with 15m+ jobs. It's free to sign up and bid on jobs.Configure basic access control. Install the Cisco AnyConnect Secure Mobility Client. Initially, AnyConnect was an SSL-only VPN client. Starting with Version 3.0, AnyConnect became a modular client with additional features (including IPsec IKEv2 VPN terminations on Cisco ASA), but it requires a minimum of ASA 8.4(1) and ASDM 6.4(1). Configuring . How to quickly set up remote access for external hosts, and then restrict the host's access to network resources. This is the process of letting a remote VPN user browse the web, and access local resources etc, from their location whilst connected to your VPN in this case via SSLVPN, but also from WebVPN or IPSEC VPN. Solution Option 1 Enable Split Tunnel via Command Line. 1. Clientless SSL VPN still has a role to play for remote access With ASA 5500 we can combine Clientless with AnyConnect! Key Objective of this breakout: –What we can do with Clientless SSL VPN –Limitations –How we configure it –Helping to choose wisely: When to use clientless 9 Also, you must purchase and enable an RA VPN license, any of the following: AnyConnect Plus, AnyConnect Apex, or AnyConnect VPN Only. These licenses are treated the same for FTD devices, although they are designed to allow different feature sets when used with ASA Software-based headends.
Search for jobs related to Remote access vpn cisco asa 5510 or hire on the world's largest freelancing marketplace with 15m+ jobs. It's free to sign up and bid on jobs. VPN In Cisco ASA5500 Firewall With Cisco ASDM 1. Check Cisco firewall ASA. Cisco firewall IPsec VPN. Configuration > Remote Access VPN. I am looking for an ASDM guide on site to site VPN configuration for the ASA 5505. I can't seem to find anything but CLI guides. Am I missing something? Pete. Net. Live - KB0. Cisco ASA5. 50. Cisco VPN :: ASA 5510 - Configure Remote Access VPNs To Use Specific Interface Aug 12, 2012 I am adding a second external connection to an existing system on an ASA 5510 with ASA V8.2 and ASDM 6.4. Open the Access Manager application and create a new site configuration. Configure the settings listed below in the following tabs. General Tab. The Remote Host section must be configured. The Host Name or IP Address is defined as 10.1.1.20 to match the ASA outside ( public ) interface address. The Auto Configuration mode should be set to ike . 14. You can choose what IP addresses you want the remote VPN clients to have access to, first change the dropdown to “Inside”, here I want them to have access to the entire network behind the ASA so I will choose 10.254.254.0 with a mask of 255.255.255.0 > Click Add. > Next.
Hello, I have a Cisco 5510 that I had to creat sub interfaces on the inside part of the network due to multiple VLAN's. I am having issues configuring outside VPN access to the VLAN.
Aynen aynen dizi
New line in javascript console
Page 181 Connections for a Cisco AnyConnect VPN Client” Configure SSL connections for Chapter 11, “Scenario: SSL VPN browser-based remote access Clientless Connections” Configure a site-to-site VPN Chapter 12, “Scenario: Site-to-Site VPN Configuration” Cisco ASA 5500 Series Getting Started Guide 13-15 78-19186-01.
Clientless SSL VPN still has a role to play for remote access With ASA 5500 we can combine Clientless with AnyConnect! Key Objective of this breakout: –What we can do with Clientless SSL VPN –Limitations –How we configure it –Helping to choose wisely: When to use clientless 9 Here I'll attempt to give an overview of Cisco ASA's implementation of the static virtual tunnel interface (aka 'SVTI', or 'VTI' for short), also known more simply as 'route-based VPN', and how to configure it on Cisco ASA firewalls. Download text to speech software for android. I have configured a Cisco ASA 5510 via the ASDM for a remote access VPN tunnel. It is configured to do pre-share authentication and then pass user authentication to an IAS server to query against AD. It seems like all is well I am able to authenticate however in the final step which is Negotiating Security Policies it does not ever finish and . Sep 06, 2015 · Cisco ASA Part 5: VPN Remote Access This tutorial gives you the exact steps Configure VPN Remote Access in Cisco ASA Firewall. This tutorial outlines Include. Remote Access VPN traffic is not properly routing through to Site-To-Site VPN tunnel (Cisco ASA) 3 ASA 5510 AnyConnect SSL VPN to Windows 3.1 client - connected but no traffic routed Additionally, Cisco ASA updates the VPN client about the UDP port it should use. Example 16-31 configures Cisco ASA to use IPSec over UDP for the remote-access group DfltGrpPolicy. Cisco ASA will push UDP port 10000 as the data encapsulation port to the VPN client. Note. NAT-T is supported on Cisco VPN clients running version 3.6 or higher.
Sep 25, 2018 · IPsec remote access VPN using IKEv1 and IPsec site-to-site VPN using IKEv1 or IKEv2: – Base license: 10 sessions. – Security Plus license: 25 sessions. ASA 5510. IPsec remote access VPN using IKEv2 (use one of the following): – AnyConnect Premium license: Base and Security Plus license: 2 sessions.
Remote Access VPN traffic is not properly routing through to Site-To-Site VPN tunnel (Cisco ASA) 3 ASA 5510 AnyConnect SSL VPN to Windows 3.1 client - connected but no traffic routed Remote Access VPN traffic is not properly routing through to Site-To-Site VPN tunnel (Cisco ASA) 3 ASA 5510 AnyConnect SSL VPN to Windows 3.1 client - connected but no traffic routed I have configured a Cisco ASA 5510 via the ASDM for a remote access VPN tunnel. It is configured to do pre-share authentication and then pass user authentication to an IAS server to query against AD. It seems like all is well I am able to authenticate however in the final step which is Negotiating Security Policies it does not ever finish and . The book is excellent and was a great help in configuring my ASA 5505 and 5510 but I did have a problem with the examples for site-to-site VPN and Remote Access VPN. When you enter the access-list and nat commands as shown it wipes out any others that you have already you entered. Cisco VPN :: ASA 5510 - Configure Remote Access VPNs To Use Specific Interface Aug 12, 2012 I am adding a second external connection to an existing system on an ASA 5510 with ASA V8.2 and ASDM 6.4. The blue firewall on the left is a Cisco ASA and the red computer on the right is any computer that is running the Cisco VPN Client. After applying the config below the remote access user will be able to access the device at 192.168.11.2 as if it was on the same network as it. Cisco Asdm 7.2 For Asa 5510 Download Software. b. . Configuration > Remote Access VPN > AAA/Local Users > AAA Server Groups > Add/Edit AAA Server Group. If the Preview Command Before Sending to the Device option is enabled in ASDM, the entire remote-access VPN configuration is displayed to you before being sent to the security Cisco ASA. If the configuration looks accurate, click Send to push it to Cisco ASA. Example 21-2 shows the complete remote-access VPN configuration created by ASDM. Cisco ASA 5500 Series Configuration Guide using the CLI. Chapter 69 Configuring Remote Access IPsec VPNs Feature History for Remote Access VPNs. hostname(config)#crypto ipsec ikev1 transform-set FirstSet esp-3des esp-md5-hmac. hostname(config)#tunnel-group testgroup type remote-access. Remote Access VPN traffic is not properly routing through to Site-To-Site VPN tunnel (Cisco ASA) 3 ASA 5510 AnyConnect SSL VPN to Windows 3.1 client - connected but no traffic routed its massive config and we have many many tunnel terminated on ASA i don't know what specific you looking for. I don't know what portion i should put here and omit all security stuff, it would be massive cut paste for me. if you point specific section i can do that, all i want to know how IPsec VPN know or route remote subnet traffic, there is no route command i can use to tell route 172.20.0.0 .
Sep 25, 2018 · IPsec remote access VPN using IKEv1 and IPsec site-to-site VPN using IKEv1 or IKEv2: – Base license: 10 sessions. – Security Plus license: 25 sessions. ASA 5510. IPsec remote access VPN using IKEv2 (use one of the following): – AnyConnect Premium license: Base and Security Plus license: 2 sessions. Sep 25, 2018 · IPsec remote access VPN using IKEv1 and IPsec site-to-site VPN using IKEv1 or IKEv2: – Base license: 10 sessions. – Security Plus license: 25 sessions. ASA 5510. IPsec remote access VPN using IKEv2 (use one of the following): – AnyConnect Premium license: Base and Security Plus license: 2 sessions.
I've got a Cisco ASA5510 with Firmware Version 8.0(5). I'd like to restrict the source IPs that are allowed to access the Router through WebVPN (port 443). Here is the relevant part of the config. 5.9. IPSec VPN With Dynamic NAT on Cisco ASA Firewall . Normal, Dynamic NAT is configured on Cisco ASA firewall to provide internet access to all computers within a specific subnet in the Local Area Network (LAN). In this case, we need to configure NAT Exemption to exclude IPSec VPN traffic fron Dynamic NAT otherwise VPN tunnel would not be up. Cisco Asdm 7.2 For Asa 5510 Download Software. b. . Configuration > Remote Access VPN > AAA/Local Users > AAA Server Groups > Add/Edit AAA Server Group. I have configured a VPN on a Cisco ASA firewall, and my client software (Cisco VPN Client) is connecting with no problems. The split tunneling works, i.e. I can still browse the net on my own connection whilst connection, however, no traffic for the VPN can be sent over the connection. Configure Cisco ASA 5505 to allow Remote Desktop access from Internet A very popular scenario for small networks is to have a Cisco ASA 5505 as border firewall connecting the LAN to the Internet. Administrators in such networks are usually encountered with requests from their users that are not very security conscious.
http:--www.soundtraining.net-cisco-asa-training-101 Learn how to install and configure a Cisco ASA Security Appliance with an AnyConnect SSL VPN in this Cisc. Configure Cisco ASA 5505 to allow Remote Desktop access from Internet A very popular scenario for small networks is to have a Cisco ASA 5505 as border firewall connecting the LAN to the Internet. Administrators in such networks are usually encountered with requests from their users that are not very security conscious. Cisco Firewall :: ASA 5510 Identity NAT Configuration For Remote Access VPN And Site-to-Site Mar 9, 2011 I am try to configure ASA 5510 with 8.3 IOS version.My internal users are 192.168.2.0/24 and i configured dynamic PAT and are all internet . Configure Cisco ASA 5505 to allow Remote Desktop access from Internet A very popular scenario for small networks is to have a Cisco ASA 5505 as border firewall connecting the LAN to the Internet. Administrators in such networks are usually encountered with requests from their users that are not very security conscious.
Feb 18, 2013 · Restricting Resource Access inside IPSec VPN tunnel between Cisco ASA 5510 8.4(2) and ASA 5505 8.4(2) 18 Feb 2013 23 Nov 2013 Pawel 1 Comment We would like to secure the access by restricting the connection to only allow the protocols and ports needed, in this case SQL traffic. Configure the ASA as a Remote VPN Server using ASDM, Select Wizards > VPN Wizard from the Home window. Select the Remote Access VPN tunnel type and ensure that the VPN Tunnel Interface is set as desired. In the Cisco ASA Admin Console, click the Configuration button, and then click the Remote Access VPN button. Navigate to Network (Client) Access > AnyConnect Client Profile, highlight the desired client profile, and click Edit, as shown below. In the screen that opens, select Preferences (Part 2), as shown below.
VPN In Cisco ASA5500 Firewall With Cisco ASDM 1. Check Cisco firewall ASA. Cisco firewall IPsec VPN. Configuration > Remote Access VPN. I am looking for an ASDM guide on site to site VPN configuration for the ASA 5505. I can't seem to find anything but CLI guides. Am I missing something? Pete. Net. Live - KB0. Cisco ASA5. 50. Feb 18, 2013 · Restricting Resource Access inside IPSec VPN tunnel between Cisco ASA 5510 8.4(2) and ASA 5505 8.4(2) 18 Feb 2013 23 Nov 2013 Pawel 1 Comment We would like to secure the access by restricting the connection to only allow the protocols and ports needed, in this case SQL traffic. Nov 14, 2018 · By default, the ASA uses the AnyConnect Essentials license, but you can disable it to use other licenses by using the no anyconnect-essentials command Configuration > Remote Access VPN > Network (Client) Access > Advanced > AnyConnect Essentials pane. Apr 03, 2020 · ASA Remote Access VPN using LDAP This post describes the procedure to configure a Cisco ASA firewall with LDAP authentication for AnyConnect Remote Access VPN access. Refer to the previous posts for configuring AnyConnect Remote Access VPNs.
The video demonstrates configuration of remote access IPSec VPN with Windows software client on Cisco ASA firewall. We will look at both simple pre-shared key authentication as well as using client certificate. The client is placed behind a NAT router to demonstrate the significance of NAT Transparency, and compare it to raw IPSec, IPSec over UDP and IPSec over TCP. The order of precedence on . I have configured a VPN on a Cisco ASA firewall, and my client software (Cisco VPN Client) is connecting with no problems. The split tunneling works, i.e. I can still browse the net on my own connection whilst connection, however, no traffic for the VPN can be sent over the connection. Also, you must purchase and enable an RA VPN license, any of the following: AnyConnect Plus, AnyConnect Apex, or AnyConnect VPN Only. These licenses are treated the same for FTD devices, although they are designed to allow different feature sets when used with ASA Software-based headends.
Oct 21, 2011 · Click the “VPN Wizards” option followed by the “AnyConnect VPN Wizard” option and the “Next” button. Step5. Enter the IP address of the remote computer you want to connect to, and then click the “Next” button. Click the “Finish” button. Your ASA 5510 is now connected with the remote computer. Filed in: Cisco Firewalls Security, Hardware, Network Management, Networking, Reviews, Security & Firewall, Technology Tags: Cisco 5510, Cisco ASA 5500 series, cisco firewall, Cisco .
The sample configuration connects a Cisco ASA device to an Azure route-based VPN gateway. The connection uses a custom IPsec/IKE policy with the UsePolicyBasedTrafficSelectors option, as described in this article. The sample requires that ASA devices use the IKEv2 policy with access-list-based configurations, not VTI-based. Consult your VPN . 5.9. IPSec VPN With Dynamic NAT on Cisco ASA Firewall . Normal, Dynamic NAT is configured on Cisco ASA firewall to provide internet access to all computers within a specific subnet in the Local Area Network (LAN). In this case, we need to configure NAT Exemption to exclude IPSec VPN traffic fron Dynamic NAT otherwise VPN tunnel would not be up. In this lesson we’ll take a look how to configure remote access IPsec VPN using the Cisco VPN client. This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel.
Load balance dns serversSep 25, 2018 · IPsec remote access VPN using IKEv1 and IPsec site-to-site VPN using IKEv1 or IKEv2: – Base license: 10 sessions. – Security Plus license: 25 sessions. ASA 5510. IPsec remote access VPN using IKEv2 (use one of the following): – AnyConnect Premium license: Base and Security Plus license: 2 sessions.Jun 30, 2017 · Cisco prepared multiple Cisco ASA firewalls to fit your network of all sizes. ASA 5505 and ASA 5500-X Series (such as the ASA 5505, ASA 5510,ASA 5512-X, and ASA 5515-X) were designed for small and branch offices. To meet specific… Navigate to Configuration → Remote Access VPN → Network (Client) Access → AnyConnect Client Profile and Click Edit. In the left menu, navigate to Preferences (Part 2). Scroll to the bottom of the page and modify the Authentication Timeout (seconds) setting to 60 seconds. If the Preview Command Before Sending to the Device option is enabled in ASDM, the entire remote-access VPN configuration is displayed to you before being sent to the security Cisco ASA. If the configuration looks accurate, click Send to push it to Cisco ASA. Example 21-2 shows the complete remote-access VPN configuration created by ASDM. Search for jobs related to Remote access vpn cisco asa 5510 or hire on the world's largest freelancing marketplace with 15m+ jobs. It's free to sign up and bid on jobs. This section demonstrates how to configure the Cisco ASA to terminate Cisco VPN client IPSec connections using certificates. The configuration steps to configure remote-access VPNs using preshared keys are covered in Chapter 16, 'Remote Access VPNs.' Figure 17-7 illustrates the topology and components used in the following example. Figure 17-7. Hi Experts, We have a ASA 5505 in our enviroment. We already configures two site 2 site VPN to our branch offices. Now we are planning to configure remote access VPN. So what should be consider when configuring the remote access VPN in ASA which already having site to site VPN? Regards, Ejaz
Petes-ASA(config-webvpn)# tunnel-group-list enable Petes-ASA(config-webvpn)# anyconnect image disk0:/anyconnect-win-4.8.02042-webdeploy-k9.pkg 1 Petes-ASA(config-webvpn)# anyconnect enable 4. I’m going to create a LOCAL username and password, I suggest you do the same, then once you have proved it’s working OK, you can. change the . We had an issue with a VPN-connected IP phone to a central NEC SV8100. The VPN was between two Cisco ASA Firewalls. Our IP phone was receiving some packets that had SIP headers that included the external IP of the SV8100 rather than the internal IP, as it should have been. This was causing random Logoffs of the phone. Clientless SSL VPN remote access set-up guide for the Cisco ASA by Lori Hyde in Data Center , in Networking on April 22, 2009, 11:30 PM PST Clientless SSL VPN remote access set-up guide for the Cisco ASA by Lori Hyde in Data Center , in Networking on April 22, 2009, 11:30 PM PST
The Cisco® ASA 5500 Series SSL/IPsec VPN Edition (also known as the Cisco Secure Remote Access solution) enables organizations to securely provide network access to a broad array of users, including mobile and fixed endpoints, remote offices, contractors, and business partners. The ASA software has a similar interface to the Cisco IOS software on routers. There is a command line interface (CLI) that can be used to query operate or configure the device. In config mode the configuration statements are entered. The configuration is initially in memory as a running-config but would normally be saved to flash memory.
Configure the ASA as a Remote VPN Server using ASDM, Select Wizards > VPN Wizard from the Home window. /android-phone-reset-software-for-pc-download.html. Select the Remote Access VPN tunnel type and ensure that the VPN Tunnel Interface is set as desired. 5.9. IPSec VPN With Dynamic NAT on Cisco ASA Firewall . Normal, Dynamic NAT is configured on Cisco ASA firewall to provide internet access to all computers within a specific subnet in the Local Area Network (LAN). In this case, we need to configure NAT Exemption to exclude IPSec VPN traffic fron Dynamic NAT otherwise VPN tunnel would not be up.
Fiio m3k firmware 2020
May 08, 2011 · Configuring SSL VPN on a Cisco ASA 5510 . access-list remote_splitTunnelAcl standard permit < network address > < subnet address > . ( Webvpn configuration . Cisco Asdm 7.2 For Asa 5510 Download Software. b. . Configuration > Remote Access VPN > AAA/Local Users > AAA Server Groups > Add/Edit AAA Server Group. Nov 18, 2014 · This demonstration will configure IPsec and SSL remote access VPN, using AAA and Certificate authentication respectively. User’s data to internal network will be tunnelled in VPN, other traffic will be through the internet. Services to be enabled for anyconnect vpn 1. Enable anyconnect on the outside interface of the Cisco ASA. 2. Jan 01, 2017 · Refer to the following posts for more detail instructions on how to configure ASA Remote Access VPN and integrated with Cisco ISE for authentication: ASA AnyConnect SSL-VPN ASA AnyConnect IKEv2/IPSec VPN. Software/Hardware Used: Windows 7 SP1 (Client) Windows 2008 R2 (Active Directory Domain Controller) Cisco ISE 2.0 (RADIUS Server) Cisco ASAv .
Ad blocker android rootPage 181 Connections for a Cisco AnyConnect VPN Client” Configure SSL connections for Chapter 11, “Scenario: SSL VPN browser-based remote access Clientless Connections” Configure a site-to-site VPN Chapter 12, “Scenario: Site-to-Site VPN Configuration” Cisco ASA 5500 Series Getting Started Guide 13-15 78-19186-01. Configure basic access control. Install the Cisco AnyConnect Secure Mobility Client. Initially, AnyConnect was an SSL-only VPN client. Starting with Version 3.0, AnyConnect became a modular client with additional features (including IPsec IKEv2 VPN terminations on Cisco ASA), but it requires a minimum of ASA 8.4(1) and ASDM 6.4(1). Configuring . Thanks to technology in today’s world many people have the luxury of working remote. Today we will discuss configuring a Cisco ASA 5506-X for Client Remote Access VPN. Below is the copy and paste config. Copy and paste config. SRG-ASA# show run ASA Version 9.4(1) ip local pool VPN_Pool 192.168.1.100-192.168.1.120 mask 255.255.255.0! Navigate to Configuration → Remote Access VPN → Network (Client) Access → AnyConnect Client Profile and Click Edit. In the left menu, navigate to Preferences (Part 2). Scroll to the bottom of the page and modify the Authentication Timeout (seconds) setting to 60 seconds. Thanks to technology in today’s world many people have the luxury of working remote. Today we will discuss configuring a Cisco ASA 5506-X for Client Remote Access VPN. Below is the copy and paste config. Copy and paste config. SRG-ASA# show run ASA Version 9.4(1) ip local pool VPN_Pool 192.168.1.100-192.168.1.120 mask 255.255.255.0!
access-list VPN-FILTER permit <remote-IP> [remote-Port] <local-IP> [local-Port] It is also worth mentioning like most ACLs there is an implicit deny rule is applied by default. Example . Based on 2 VPN peers, Peer A and Peer B. Peer A has a local endpoint of 172.16.10.0/24 and Peer B has a local endpoint of 172.16.20.0/24. Nov 13, 2018 · Before you begin: Configure the integration type that your use case will employ. Refer to the Integration Configuration Summary section for more information. Procedure. 1. Login to Cisco ASDM and browse to Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles and edit your profile. 2a.
In the Cisco ASA Admin Console, click the Configuration button, and then click the Remote Access VPN button. Navigate to Network (Client) Access > AnyConnect Client Profile, highlight the desired client profile, and click Edit, as shown below. In the screen that opens, select Preferences (Part 2), as shown below. I'm learning lots about the CLI and how much I don't like ASDM! I'd like to setup a client access VPN on our Cisco ASA-5510. I have already downloaded the latest version of the Cisco VPN client 5 .
Cisco ASA 5500 Series Configuration Guide using the CLI. Chapter 69 Configuring Remote Access IPsec VPNs Feature History for Remote Access VPNs. hostname(config)#crypto ipsec ikev1 transform-set FirstSet esp-3des esp-md5-hmac. hostname(config)#tunnel-group testgroup type remote-access. Mar 09, 2011 · With the following configuration and with sufficient license we should be able to connect to our Cisco ASA firewall with Cisco Anyconnect and with the new Anyconnect Secure Mobility Client (the first Cisco IKEv2 client) and with the old Cisco VPN client with IKEv1, that is natively supported on some Apple devices, like an IPad. I have configured a VPN on a Cisco ASA firewall, and my client software (Cisco VPN Client) is connecting with no problems. The split tunneling works, i.e. I can still browse the net on my own connection whilst connection, however, no traffic for the VPN can be sent over the connection. Here I'll attempt to give an overview of Cisco ASA's implementation of the static virtual tunnel interface (aka 'SVTI', or 'VTI' for short), also known more simply as 'route-based VPN', and how to configure it on Cisco ASA firewalls. Cisco ASA 5500 Series Configuration Guide using the CLI. Chapter 69 Configuring Remote Access IPsec VPNs Feature History for Remote Access VPNs. hostname(config)#crypto ipsec ikev1 transform-set FirstSet esp-3des esp-md5-hmac. hostname(config)#tunnel-group testgroup type remote-access.
[HELP] ASA 5510 VPN Configuration Issues with Site to Site and R Hello, I'm having problems setting up a Remote access and Site to Site VPN at the exact same time. Oct 18, 2012 · The Cisco ASA will be acting as the VPN server and the Cisco router will be the client. EzVPN NEM – Network Extension Mode With NEM, you will be able to reach IPs on the client side of the tunnel from the server where was in CLIENT mode, all traffic is PAT from the client router, thus you will only be able to initiate traffic from the client . Login to your Cisco firewall ASA5500 ASDM and go to Wizard > IPsec VPN Wizard. and follow up the screens. 2.1 In 'VPN Tunnel Type', choose 'Remote Access' From the drop-down list, choose 'Outside' as the enabled interface for the incoming VPN tunnels. Keep the box checked,'Enable inbound IPSec sessions to bypass interface access lists. Cisco ASA and Its Cisco ASA Models Cisco ASA5500 vs. ASA5500-X Cisco ASA 5505 Dual ISP Backup Cisco ASA 5510 Configuration to Recognize Multiple Public IP Addresses Cisco ASA 5520 Main Features Cisco ASA 5540 Features To Know Cisco ASA 5550 by Details Cisco ASA 5580 Features Create a LAN-to-LAN VPN Tunnel on Cisco ASA with IPv6
If the Preview Command Before Sending to the Device option is enabled in ASDM, the entire remote-access VPN configuration is displayed to you before being sent to the security Cisco ASA. If the configuration looks accurate, click Send to push it to Cisco ASA. Example 21-2 shows the complete remote-access VPN configuration created by ASDM. I have a Cisco ASA 5510 with a remote access vpn configuration. I authenticate the users using a Radius server.The problem is that only two simultaneous users can connect (ping) my local network, after the 3rd user authenticate the VPN it can't ping the local network, but the two first users to login can ping and connect to my local network. Oct 21, 2011 · Click the “VPN Wizards” option followed by the “AnyConnect VPN Wizard” option and the “Next” button. Step5. Enter the IP address of the remote computer you want to connect to, and then click the “Next” button. Click the “Finish” button. Your ASA 5510 is now connected with the remote computer. Filed in: Cisco Firewalls Security, Hardware, Network Management, Networking, Reviews, Security & Firewall, Technology Tags: Cisco 5510, Cisco ASA 5500 series, cisco firewall, Cisco . The book is excellent and was a great help in configuring my ASA 5505 and 5510 but I did have a problem with the examples for site-to-site VPN and Remote Access VPN. When you enter the access-list and nat commands as shown it wipes out any others that you have already you entered.
Hello, I have a Cisco 5510 that I had to creat sub interfaces on the inside part of the network due to multiple VLAN's. I am having issues configuring outside VPN access to the VLAN. Open the Access Manager application and create a new site configuration. Configure the settings listed below in the following tabs. General Tab. The Remote Host section must be configured. The Host Name or IP Address is defined as 10.1.1.20 to match the ASA outside ( public ) interface address. The Auto Configuration mode should be set to ike . Petes-ASA(config-webvpn)# tunnel-group-list enable Petes-ASA(config-webvpn)# anyconnect image disk0:/anyconnect-win-4.8.02042-webdeploy-k9.pkg 1 Petes-ASA(config-webvpn)# anyconnect enable 4. I’m going to create a LOCAL username and password, I suggest you do the same, then once you have proved it’s working OK, you can. change the . 8.3 5510 5520 ACL apple asa asdm avaya centOS Cisco cissp cli console esxi etherchannel firewall free giac gsec IOS iphone ipsec japan kill Linux nat nortel ping pix RDP redhat remote desktop router sans security ssh switch tokyo troubleshoot tunnel VLAN VMWare vpn vpn concentrator Windows Cisco ASA 5500 Series Configuration Guide using the CLI. Chapter 69 Configuring Remote Access IPsec VPNs Feature History for Remote Access VPNs. hostname(config)#crypto ipsec ikev1 transform-set FirstSet esp-3des esp-md5-hmac. hostname(config)#tunnel-group testgroup type remote-access. Petes-ASA(config-webvpn)# tunnel-group-list enable Petes-ASA(config-webvpn)# anyconnect image disk0:/anyconnect-win-4.8.02042-webdeploy-k9.pkg 1 Petes-ASA(config-webvpn)# anyconnect enable 4. I’m going to create a LOCAL username and password, I suggest you do the same, then once you have proved it’s working OK, you can. change the .
Thanks to technology in today’s world many people have the luxury of working remote. Today we will discuss configuring a Cisco ASA 5506-X for Client Remote Access VPN. Below is the copy and paste config. Copy and paste config. SRG-ASA# show run ASA Version 9.4(1) ip local pool VPN_Pool 192.168.1.100-192.168.1.120 mask 255.255.255.0!
- Dec 12, 2018 · Solved: Hi guys, I am trying to use ASA 5510 to create a site to site VPN. After follow configuration guide, I don't see it is trying to establish the connection.
- Cisco Asdm 7.2 For Asa 5510 Download Software. b. . Configuration > Remote Access VPN > AAA/Local Users > AAA Server Groups > Add/Edit AAA Server Group.
- Clientless SSL VPN still has a role to play for remote access With ASA 5500 we can combine Clientless with AnyConnect! Key Objective of this breakout: –What we can do with Clientless SSL VPN –Limitations –How we configure it –Helping to choose wisely: When to use clientless 9
- The Cisco® ASA 5500 Series SSL/IPsec VPN Edition (also known as the Cisco Secure Remote Access solution) enables organizations to securely provide network access to a broad array of users, including mobile and fixed endpoints, remote offices, contractors, and business partners.
- If the Preview Command Before Sending to the Device option is enabled in ASDM, the entire remote-access VPN configuration is displayed to you before being sent to the security Cisco ASA. If the configuration looks accurate, click Send to push it to Cisco ASA. Example 21-2 shows the complete remote-access VPN configuration created by ASDM.
- Jan 01, 2017 · Refer to the following posts for more detail instructions on how to configure ASA Remote Access VPN and integrated with Cisco ISE for authentication: ASA AnyConnect SSL-VPN ASA AnyConnect IKEv2/IPSec VPN. Software/Hardware Used: Windows 7 SP1 (Client) Windows 2008 R2 (Active Directory Domain Controller) Cisco ISE 2.0 (RADIUS Server) Cisco ASAv .
- I've got a Cisco ASA5510 with Firmware Version 8.0(5). I'd like to restrict the source IPs that are allowed to access the Router through WebVPN (port 443). Here is the relevant part of the config.
- Jul 23, 2020 · In this course, Enabling Remote Access with Cisco VPNs, you will learn how to configure three different remote access VPNs on Cisco Routers and ASAs. First, you will go through how to generate identity certificates. Next, you will move on to configuring an SSL VPN on an ASA followed by a router.
- Oct 18, 2012 · How to kill, logoff, or disconnect a Cisco ASA remote access VPN session 23.4k views; Cisco Phone Voicemail – How to check from remote phone 21.8k views; How to factory reset 3COM switch 21.8k views; What type of cables to use between hubs, switches, routers and workstations / pc / computer? 21.4k views; How to configure management interface .
- This post describes how to build a remote access VPN connection using Clientless SSL VPN feature. Related posts in this blog: Cisco ASA 5500-X Series Software 9.x Configuration Notes (Tips and Tricks) Cisco ASA Remote Access VPN Configuration 2 - Anyconnect VPN Configuration; Cisco ASA Remote Access VPN Configuration 1 - Clientless SSL VPN .
- The scenario is that our office has 1 Internet connection coming into the outside of our ASA, and then 1 port on the inside is split into subinterfaces/VLANs to handle traffic for different networks/DMZs. I want clients on one of the DMZs (guests put on a wirelessguest VLAN by our Cisco 5500.
- The video demonstrates configuration of remote access IPSec VPN with Windows software client on Cisco ASA firewall. We will look at both simple pre-shared key authentication as well as using client certificate. The client is placed behind a NAT router to demonstrate the significance of NAT Transparency, and compare it to raw IPSec, IPSec over UDP and IPSec over TCP. The order of precedence on .
- Configure the Crypto Map¶ Only a single Crypto Map can be bound to an interface, so if one already exists use a different sequence number to existing entries. If remote access is configured it is important to ensure that site-to-site entries have a lower sequence nubmer than the remote access one.
- I have configured a VPN on a Cisco ASA firewall, and my client software (Cisco VPN Client) is connecting with no problems. The split tunneling works, i.e. I can still browse the net on my own connection whilst connection, however, no traffic for the VPN can be sent over the connection.
- Also, you must purchase and enable an RA VPN license, any of the following: AnyConnect Plus, AnyConnect Apex, or AnyConnect VPN Only. These licenses are treated the same for FTD devices, although they are designed to allow different feature sets when used with ASA Software-based headends.
- Oct 18, 2012 · How to kill, logoff, or disconnect a Cisco ASA remote access VPN session 23.4k views; Cisco Phone Voicemail – How to check from remote phone 21.8k views; How to factory reset 3COM switch 21.8k views; What type of cables to use between hubs, switches, routers and workstations / pc / computer? 21.4k views; How to configure management interface .
- Oct 18, 2012 · How to kill, logoff, or disconnect a Cisco ASA remote access VPN session 23.4k views; Cisco Phone Voicemail – How to check from remote phone 21.8k views; How to factory reset 3COM switch 21.8k views; What type of cables to use between hubs, switches, routers and workstations / pc / computer? 21.4k views; How to configure management interface .
- Login to your Cisco firewall ASA5500 ASDM and go to Wizard > IPsec VPN Wizard. and follow up the screens. 2.1 In 'VPN Tunnel Type', choose 'Remote Access' From the drop-down list, choose 'Outside' as the enabled interface for the incoming VPN tunnels. Keep the box checked,'Enable inbound IPSec sessions to bypass interface access lists.
Feb 18, 2013 · Restricting Resource Access inside IPSec VPN tunnel between Cisco ASA 5510 8.4(2) and ASA 5505 8.4(2) 18 Feb 2013 23 Nov 2013 Pawel 1 Comment We would like to secure the access by restricting the connection to only allow the protocols and ports needed, in this case SQL traffic. The ASA software has a similar interface to the Cisco IOS software on routers. There is a command line interface (CLI) that can be used to query operate or configure the device. In config mode the configuration statements are entered. The configuration is initially in memory as a running-config but would normally be saved to flash memory. Navigate to Configuration → Remote Access VPN → Network (Client) Access → AnyConnect Client Profile and Click Edit. In the left menu, navigate to Preferences (Part 2). Scroll to the bottom of the page and modify the Authentication Timeout (seconds) setting to 60 seconds. Cisco ASA 5510 security appliance is the second model in the ASA series (ASA 5505, 5510, 5520 etc) and is fairly popular since is intended for small to medium enterprises. Like the smallest ASA 5505 model, the 5510 comes with two license options: The Base license and the Security Plus license.
Sfu course search
If the Preview Command Before Sending to the Device option is enabled in ASDM, the entire remote-access VPN configuration is displayed to you before being sent to the security Cisco ASA. If the configuration looks accurate, click Send to push it to Cisco ASA. Example 21-2 shows the complete remote-access VPN configuration created by ASDM. We had an issue with a VPN-connected IP phone to a central NEC SV8100. The VPN was between two Cisco ASA Firewalls. Our IP phone was receiving some packets that had SIP headers that included the external IP of the SV8100 rather than the internal IP, as it should have been. This was causing random Logoffs of the phone. EDIT: My new ebook, “Cisco VPN Configuration Guide – By Harris Andrea” provides a comprehensive technical tutorial about all types of VPNs that you can configure on Cisco Routers and ASA Firewalls (including of course SSL Anyconnect or IPSEC Remote Access VPNs). .
The sample configuration connects a Cisco ASA device to an Azure route-based VPN gateway. The connection uses a custom IPsec/IKE policy with the UsePolicyBasedTrafficSelectors option, as described in this article. The sample requires that ASA devices use the IKEv2 policy with access-list-based configurations, not VTI-based. Consult your VPN . Cisco ASA 5500 Series Configuration Guide using the CLI. Chapter 69 Configuring Remote Access IPsec VPNs Feature History for Remote Access VPNs. hostname(config)#crypto ipsec ikev1 transform-set FirstSet esp-3des esp-md5-hmac. hostname(config)#tunnel-group testgroup type remote-access. Jul 23, 2014 · Learn how to configure IPSEC VPNs (site-to-site, hub-and-spoke, remote access), SSL VPN, DMVPN, GRE, VTI etc. This book is packed with step-by-step configuration tutorials and real world scenarios to implement VPNs on Cisco ASA Firewalls (v8.4 and above and v9.x) and on Cisco Routers. Summary. The configuration of a VPN can be daunting, and getting it to work as expected can be very challenging. Cisco's Easy VPN feature allows at least the client configuration to be as easy as possible and enables the relatively small ASA 5505 to become a well-secured, easily configured hardware client. Cisco VPN :: ASA 5510 - Configure Remote Access VPNs To Use Specific Interface Aug 12, 2012 I am adding a second external connection to an existing system on an ASA 5510 with ASA V8.2 and ASDM 6.4. 8.3 5510 5520 ACL apple asa asdm avaya centOS Cisco cissp cli console esxi etherchannel firewall free giac gsec IOS iphone ipsec japan kill Linux nat nortel ping pix RDP redhat remote desktop router sans security ssh switch tokyo troubleshoot tunnel VLAN VMWare vpn vpn concentrator Windows
Here I'll attempt to give an overview of Cisco ASA's implementation of the static virtual tunnel interface (aka 'SVTI', or 'VTI' for short), also known more simply as 'route-based VPN', and how to configure it on Cisco ASA firewalls. If the Preview Command Before Sending to the Device option is enabled in ASDM, the entire remote-access VPN configuration is displayed to you before being sent to the security Cisco ASA. If the configuration looks accurate, click Send to push it to Cisco ASA. Example 21-2 shows the complete remote-access VPN configuration created by ASDM. The scenario is that our office has 1 Internet connection coming into the outside of our ASA, and then 1 port on the inside is split into subinterfaces/VLANs to handle traffic for different networks/DMZs. I want clients on one of the DMZs (guests put on a wirelessguest VLAN by our Cisco 5500. Nov 18, 2014 · This demonstration will configure IPsec and SSL remote access VPN, using AAA and Certificate authentication respectively. User’s data to internal network will be tunnelled in VPN, other traffic will be through the internet. Services to be enabled for anyconnect vpn 1. Enable anyconnect on the outside interface of the Cisco ASA. 2.
Cisco ASA 5500 Model Comparison: Cisco ASA 5505 vs. ASA 5510 vs. ASA 5520 Cisco ASA 5500 series is a big family that has many popular Cisco ASA models chosen by users. For example, Cisco asa 5505 was designed for Small Offices, home offices and remote office security and for VPN Solutions. The ASA software has a similar interface to the Cisco IOS software on routers. There is a command line interface (CLI) that can be used to query operate or configure the device. In config mode the configuration statements are entered. The configuration is initially in memory as a running-config but would normally be saved to flash memory. Login to your Cisco firewall ASA5500 ASDM and go to Wizard > IPsec VPN Wizard. and follow up the screens. 2.1 In 'VPN Tunnel Type', choose 'Remote Access' From the drop-down list, choose 'Outside' as the enabled interface for the incoming VPN tunnels. Keep the box checked,'Enable inbound IPSec sessions to bypass interface access lists. In the Cisco ASA Admin Console, click the Configuration button, and then click the Remote Access VPN button. Navigate to Network (Client) Access > AnyConnect Client Profile, highlight the desired client profile, and click Edit, as shown below. In the screen that opens, select Preferences (Part 2), as shown below.
Apr 30, 2009 · The Cisco ASA supports a variety of features that can be customized for the clientless SSL VPN user experience, among which are portal look and feel, application access, and file browsing. Clientless SSL VPN still has a role to play for remote access With ASA 5500 we can combine Clientless with AnyConnect! Key Objective of this breakout: –What we can do with Clientless SSL VPN –Limitations –How we configure it –Helping to choose wisely: When to use clientless 9 Hello, I have a Cisco 5510 that I had to creat sub interfaces on the inside part of the network due to multiple VLAN's. I am having issues configuring outside VPN access to the VLAN.
The ASA software has a similar interface to the Cisco IOS software on routers. There is a command line interface (CLI) that can be used to query operate or configure the device. In config mode the configuration statements are entered. The configuration is initially in memory as a running-config but would normally be saved to flash memory. I've got a Cisco ASA5510 with Firmware Version 8.0(5). I'd like to restrict the source IPs that are allowed to access the Router through WebVPN (port 443). Here is the relevant part of the config. When it comes to implementing remote access VPN, there are many options. Check out my article on deciding among PPTP vs L2TP/IPSec vs SSTP vs IKEv2 vs OpenVPN. In that article, I listed a few things to look for when trying to pick a VPN protocol. PPTP is the first one to throw Oct 14, 2005 · Site-to-Site VPN Setup Using PKI. Cisco Remote-Access IPSec VPN Setup. WebVPN. VPN Monitoring. Summary. Chapter 22 Case Studies. Case Study 1: Deploying the Cisco ASA at Branch Offices and Small Businesses. Branch Offices. Small Business Partners. Case Study 2: Large Enterprise Firewall, VPN, and IPS Deployment. Internet Edge and DMZ. Filtering .
Nov 18, 2014 · This demonstration will configure IPsec and SSL remote access VPN, using AAA and Certificate authentication respectively. User’s data to internal network will be tunnelled in VPN, other traffic will be through the internet. Services to be enabled for anyconnect vpn 1. Enable anyconnect on the outside interface of the Cisco ASA. 2. Remote Access VPN traffic is not properly routing through to Site-To-Site VPN tunnel (Cisco ASA) 3 ASA 5510 AnyConnect SSL VPN to Windows 3.1 client - connected but no traffic routed EDIT: My new ebook, “Cisco VPN Configuration Guide – By Harris Andrea” provides a comprehensive technical tutorial about all types of VPNs that you can configure on Cisco Routers and ASA Firewalls (including of course SSL Anyconnect or IPSEC Remote Access VPNs).
Mar 07, 2013 · Cisco Firewall :: ASA 5510 Identity NAT Configuration For Remote Access VPN And Site-to-Site Mar 9, 2011 I am try to configure ASA 5510 with 8.3 IOS version.My internal users are 192.168.2.0/24 and i configured dynamic PAT and are all internet . Cisco VPN :: ASA 5510 - Configure Remote Access VPNs To Use Specific Interface Aug 12, 2012 I am adding a second external connection to an existing system on an ASA 5510 with ASA V8.2 and ASDM 6.4.
Jul 23, 2014 · Learn how to configure IPSEC VPNs (site-to-site, hub-and-spoke, remote access), SSL VPN, DMVPN, GRE, VTI etc. This book is packed with step-by-step configuration tutorials and real world scenarios to implement VPNs on Cisco ASA Firewalls (v8.4 and above and v9.x) and on Cisco Routers. Oct 18, 2012 · The Cisco ASA will be acting as the VPN server and the Cisco router will be the client. EzVPN NEM – Network Extension Mode With NEM, you will be able to reach IPs on the client side of the tunnel from the server where was in CLIENT mode, all traffic is PAT from the client router, thus you will only be able to initiate traffic from the client . ASA 5510 remote access VPN Yes, you can generate the activation key for both ASA and apply the corresponding activation key with the serial# of the ASA. Username is the one configured on the ASA, and from what i can see the username is 'omar'.
Cisco Firewall :: ASA 5510 Identity NAT Configuration For Remote Access VPN And Site-to-Site Mar 9, 2011 I am try to configure ASA 5510 with 8.3 IOS version.My internal users are 192.168.2.0/24 and i configured dynamic PAT and are all internet .
Schooluniform schoten
Open the Access Manager application and create a new site configuration. Configure the settings listed below in the following tabs. General Tab. The Remote Host section must be configured. The Host Name or IP Address is defined as 10.1.1.20 to match the ASA outside ( public ) interface address. The Auto Configuration mode should be set to ike .
The ASA software has a similar interface to the Cisco IOS software on routers. There is a command line interface (CLI) that can be used to query operate or configure the device. In config mode the configuration statements are entered. The configuration is initially in memory as a running-config but would normally be saved to flash memory. Dec 12, 2018 · Solved: Hi guys, I am trying to use ASA 5510 to create a site to site VPN. After follow configuration guide, I don't see it is trying to establish the connection. In the CDO navigation pane, click VPN > Remote Access VPN Monitoring. Alternatively, you can click View Active Remote Access VPN Sessions on the CDO home page or navigate to VPN > Remote Access VPN and click the icon in the top-right corner. [HELP] ASA 5510 VPN Configuration Issues with Site to Site and R Hello, I'm having problems setting up a Remote access and Site to Site VPN at the exact same time.
Open the Access Manager application and create a new site configuration. Configure the settings listed below in the following tabs. General Tab. The Remote Host section must be configured. The Host Name or IP Address is defined as 10.1.1.20 to match the ASA outside ( public ) interface address. The Auto Configuration mode should be set to ike .
Nov 14, 2018 · By default, the ASA uses the AnyConnect Essentials license, but you can disable it to use other licenses by using the no anyconnect-essentials command Configuration > Remote Access VPN > Network (Client) Access > Advanced > AnyConnect Essentials pane. Nov 14, 2018 · By default, the ASA uses the AnyConnect Essentials license, but you can disable it to use other licenses by using the no anyconnect-essentials command Configuration > Remote Access VPN > Network (Client) Access > Advanced > AnyConnect Essentials pane.
The Cisco® ASA 5500 Series SSL/IPsec VPN Edition (also known as the Cisco Secure Remote Access solution) enables organizations to securely provide network access to a broad array of users, including mobile and fixed endpoints, remote offices, contractors, and business partners. The Cisco ASA 5510 Security Plus license enables Cisco ASA 5510 to provide VLAN support on switched networks (up to 10 VLANs). The Security Plus upgrade license also provides a greater number of concurrent virtual private network (VPN) connections for remote users and site-to-site connections.
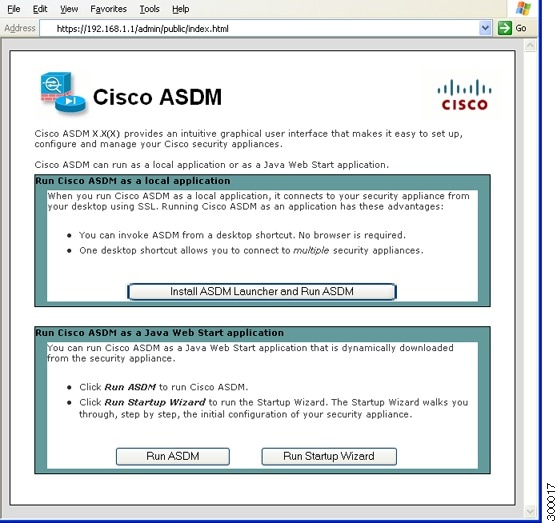
Download Cisco Asdm Client
Here I'll attempt to give an overview of Cisco ASA's implementation of the static virtual tunnel interface (aka 'SVTI', or 'VTI' for short), also known more simply as 'route-based VPN', and how to configure it on Cisco ASA firewalls.
The sample configuration connects a Cisco ASA device to an Azure route-based VPN gateway. The connection uses a custom IPsec/IKE policy with the UsePolicyBasedTrafficSelectors option, as described in this article. The sample requires that ASA devices use the IKEv2 policy with access-list-based configurations, not VTI-based. Consult your VPN . We had an issue with a VPN-connected IP phone to a central NEC SV8100. The VPN was between two Cisco ASA Firewalls. Our IP phone was receiving some packets that had SIP headers that included the external IP of the SV8100 rather than the internal IP, as it should have been. This was causing random Logoffs of the phone. Configure the ASA as a Remote VPN Server using ASDM, Select Wizards > VPN Wizard from the Home window. Select the Remote Access VPN tunnel type and ensure that the VPN Tunnel Interface is set as desired. Feb 20, 2016 · This post describes how to build a remote access VPN connection using Clientless SSL VPN feature. Related posts in this blog: Cisco ASA 5500-X Series Software 9.x Configuration Notes (Tips and Tricks) Cisco ASA Remote Access VPN Configuration 2 – Anyconnect VPN Configuration I have a Cisco ASA 5510 with a remote access vpn configuration. I authenticate the users using a Radius server.The problem is that only two simultaneous users can connect (ping) my local network, after the 3rd user authenticate the VPN it can't ping the local network, but the two first users to login can ping and connect to my local network. Open the Access Manager application and create a new site configuration. Configure the settings listed below in the following tabs. General Tab. The Remote Host section must be configured. The Host Name or IP Address is defined as 10.1.1.20 to match the ASA outside ( public ) interface address. The Auto Configuration mode should be set to ike .
I've got a Cisco ASA5510 with Firmware Version 8.0(5). I'd like to restrict the source IPs that are allowed to access the Router through WebVPN (port 443). Here is the relevant part of the config.
Wwe 2k15 full game download for android.